Title: Getting to Know SIEM Definition, How it Works, and the Difference with SOAR For You. Get More Information from our site @iwanrj.com free.
Threats of cyber attacks have increasingly diverse and greater motivations that drive companies to increase security measures. A pandemic that forces people to work from home is increasingly becoming a challenge for businesses as the threat of security vulnerabilities increases.
More and more industries are moving services and systems online, enabling intruders and cyber attacks. An antivirus program alone is not enough. Now is the time to equip it with SIEM to prevent potential cyber attacks and detect anomalies in applications and services.
SIEM software and tools protect your business by detecting threats, ensuring compliance, and managing other cybersecurity issues in your network environment.
SIEM works in real time to minimize the presence of intruders or malware in the system, which can be detected and fixed quickly. Learn more about SIEM and how it can benefit your business.
SIEM definition:
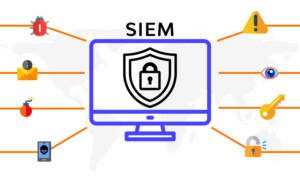
Security Information and Event Management (SIEM) is a tool for monitoring network traffic for cyber threats or attacks and analyzing logs generated by applications or devices in real time.
SIEM enables early detection of potential cyber attacks in real-time, records events for future reference, and correlates events from all sources to trace intrusion paths.
In addition, SIEM can also be a log management system that collects logs from servers, networks, firewalls, databases, and more.
SIEM typically goes through four processes when it detects a potential cyber attack, starting with data collection (in the form of hackers, firewalls, etc.i
n real time from network devices, domain controllers, and routers) and data aggregation (optimizing processes and correlates to similar cases). ). , analysis (alerts IT team to distinguish between potentially harmful and non-hazardous data), breach identification and resolution (identification and resolution to ensure no similar breach exists).
In general, SIEM provides two monitoring outputs, namely reports and warnings. SIEM reports capture and display security incidents, ranging from malicious activity to failed login attempts.
Meanwhile, when the analysis engine successfully detects suspicious activity, the SIEM alert function will be activated.
SIEM can help improve detection and response times by aggregating and normalizing business data. In addition, SIEM also helps accelerate threat detection, investigation, and security alerts.
Additionally, SIEM can display application, infrastructure, and network logs from all host systems in a single interface.
This allows security and DevOps teams to detect attacks and control attack attempts via web components. Centralized log information helps identify hosts affected by attacks.
SIEM devices are often equipped with automated mechanisms to provide notification of potential violations. SIEM can respond automatically to stop attacks while they are still happening, including taking potentially compromised servers offline to minimize the impact of a breach.
How SIEMs Work
SIEM is created by combining Security Information Management (SIM) and Security Event Management (SEM). SIM focus on deep data collection log filesfor the purposes of analysis and reports on the system by combining logs and threat intelligence.
Meanwhile, SEM handles security incidents in a seamless manner real-time provided by Intruder Detection Systems (IDS), firewallsand antivirus systems, to provide warnings so that the threat can be dealt with immediately.
Modern SIEM solutions can analyze multiple data sources from:
- Any application the company uses.
- Network devices such as routers, switches, bridges, wireless access points, modem, line driversAnd hubs.
- servers like web, proxies, mail, And file transfer protocol.
- Security devices such as IDP/IPS, firewallsanti virus software, And content filters.
Logs generated by security device applications such as servers, network, firewalls, databases, and others in every instance, including when there are maintenance because the s/w installation will show in SYSLOG. If the security device encounters some security warning, it will generate logs.
Similarly, when all applications (log sources) experience certain events, it generates logs. The resulting logs will be sent by each application or centralized security device to SIEM. To collect large volumes of logs, you can install a configurable collector in the app to facilitate log delivery to SIEM.
However, the raw logs generated from all applications are difficult to read or analyze. SIEM can help analyze raw logs and generate the necessary information.
SIEM will collect logs of several different security applications and devices to be managed as a single log store. In general, size logs depending on the level of network traffic. Big data plays an important role in analysis logs collected in SIEM.
The difference between SIEM and SOAR
SOAR comes from the acronym for Security Orchestra Automation and Response. Overall, SOAR is a new approach to security operations, especially incident handling.
SOAR has the benefit of increasing the efficiency, speed, availability, and stability of security operations.
SOAR has tools that can integrate all tools and applications into the company’s security system, enable the security team to automate the response process when a security breach occurs, and can identify potential threat vulnerabilities through the resolution process.
Then what is the difference from SIEM And SOAR This? Let’s see the difference based on 3 things, as follows:
1. Core Functions and Capabilities
SIEM
- Target data storage, security intelligence, and analytics needs.
- Use of data aggression, threat detection, identification and notification.
- The process is not automated and requires human participation at the final stage.
- Triggers increased alerts when suspicious activity is detected.
- Requires manual security analysis to determine if further investigation is necessary.
- As well as reporting the findings as an incident.
SOAR
- Run all processes automatically.
- Has the ability to declare an event as a security incident or just an ordinary, harmless event.
2. Human Intervention
SIEM
- It needs constant improvement and development, so that the Security team can maximize its function
- Although built to save time, the system can be a waste of time as it requires a team to manage, maintain operations and differentiate alert types.
SOAR
- Helps minimize human participation, because automation is the main goal.
- Able to filter out “fake” attacks, the system generates few alerts allowing security analysts to focus on improving and automating more incident response plans
- But to overcome mission critical system still need approval from experts or humans.
3. Data Source
SIEM
- The use of the same type of data, namely data logs and events across all application and network components.
- The various sources of data and the amount collected are different.
- Data set logs and events from hosts and infrastructure resources (firewall, Data loss prevention tooldetection and prevention system malware).
- Integration of various data sources including external applications to combine many types of data.
SOAR
- The use of the same type of data, namely data logs and events across all application and network components
- The various sources of data and the amount collected are different
- Based on the purpose of automation, the system needs to have a lot of knowledge related to network configuration and actions to identify anomalies.
It is essential to implement multiple SIEM tools and software so that IT security teams can easily detect cyber threats before they attack applications and devices. The SIEM system will alert the IT team so they have time to take action to prevent attacks before damage occurs.
The IT team must be engaged manually to decide on further action, whether to conduct a thorough investigation, and whether to classify the finding as an incident. SIEM tools also provide a way to automate protection within the system, freeing organizations from potential human error in spotting potential threats.
At the same time, SIEM uses data aggregation, threat detection, identification and notification. However, all of these late-stage processes still require human involvement as they cannot be automated.
Warning to customers: Collect logs for review to prevent similar attacks in the future. In addition, an audit is needed to normalize data so that IT managers can carry out infrastructure maintenance.
6 Advantages of using SIEM
- Increase efficiency in detecting and responding to threats.
- Reducing the cost and impact of cyber attacks.
- Prevent current and future attacks by logging.
- Real-time notifications so they can respond quickly to attacks.
- Reducing labor costs and information security.
- Help comply with cyber security industry standards and regulations.
Leverage SIEM to Overcome Cyber Attacks
The SIEM system collects information from multiple sources about an organization’s network infrastructure, including servers, systems, devices, and applications, to identify potential external and internal threats.
Modern SIEM solutions provide a “centralized view” that combines contextual information about users, enterprise resources and more.
It’s high time you leverage modern SIEM to counter potential cyber attacks or other increasingly complex security issues. Unlike traditional SIEM, modern SIEM provides complete visibility into all networks, applications and hardware.
SIEM is a solution for analyzing large amounts of data and finding activity that can trigger an attack in seconds. This advantage is one of the plus points that traditional SIEM does not offer.