Title: Definition, Types, and How to Avoid Cyber Hack
For You. Get More Information from our site @iwanrj.com free.
When we hear the term cyber hack, the first thing that comes to our mind is usually online crimes such as cyber hacks. But, this time we will not discuss it in general, but specifically cyber hacking. Cyber hack is an attack carried out by hackers with a specific system and purpose. What is a cyber hack like, types, and how to avoid it? Check out the following article.
Definition of Cyber Hacking
Cyber hacks is an online attack carried out by hackers on a company, organization or system with a specific purpose. These actors can be individuals or groups.
This attack can cause the death of computer equipment, data theft, or the use of the victim’s computer as an engine for distributing other attacks, such as viruses, malware, DoS, spyware, ransomware, social engineering, and many more.
Cyber hacking is an activity that violates the terms of use of services and social norms in cyberspace, and can cause harm to the victim who is the target. The activities of this cybercrime have many motivations and various attack methods according to predetermined targets or even carried out randomly.
Here are some examples of common cyberattacks and types of data breaches:
- Identity theft, fraud, extortion.
- Malware, phishing, spamming, spoofing, spyware, trojans and viruses.
- Stolen hardware, such as a laptop or mobile device.
- Denial-of-service (DoS) and distributed denial-of-service attacks.
- Access violation.
- Password theft. System infiltration.
- Website tampering.
- Private and public browser exploits.
- Misuse of short/instant messages (SMS, WA, Telegram, etc.).
- Intellectual property (IP) theft or unauthorized access.
Types of Cyber Hacks
After knowing what a cyber hack is, you should already know what the activity looks like, so below are several types of cyber hacks whose practice is increasingly widespread.
1. Identity theft
Cyber hack is identity theft or identity theft against a person. Usually the perpetrators will hack the site owned by the victim, after that they will access the server and get the person’s information.
Identity theft is mostly found on online shop sites or membership websites that have a lot of customer data. From the information that has been obtained, the perpetrator will usually use it for harmful things.
2. Carding
Carding is credit card burglary by stealing the information data and then using it for personal gain. This type of cyber hack is being found and is killing victims.
The impact that will be felt the most if you don’t immediately realize this hack is that you will be asked to pay large bills for expenses that you have never done.
3. Corporate data theft
Corporate data theft is almost the same as identity theft, only this type attacks companies. Usually the perpetrators will hack the company’s site or system and then steal important data.
The data will be used for personal gain and can even be sold on the black market at fantastic prices.
4. Cyber extortion
Cyber extortion, in which the perpetrator uses extortion by demanding a ransom for stolen data. These cases are usually marked by installing malware or ransomware on the victim’s device.
After that the perpetrator will control the data on the device. If the victim wants to access the device again, he must provide the ransom money.
5. Cyber espionage
Cyber espionage or spy. In this case the perpetrator will spy on the targeted target, whether it’s a competitor, political opponent, or something else. This espionage is carried out online, one of which is by utilizing spyware.
How Cyber Hacks Work
After understanding what types of cyber hacks are commonly found, then how do cyber hacks work and hack sites or victim’s personal data.
In practice, perpetrators take advantage of malware attacks to steal user data in the cloud. If the cloud has been successfully hacked, the system will transfer commands to the modules that were made by the previous actor.
In addition, attacks can also be carried out by sending malicious activities such as stealing data or spying on company activities.
The most common malware attacks today are SQL multisite and script attacks. During scripting on websites, perpetrators will usually add malicious code to weaken the site.
How to Avoid Cyber Hacks
As you know, cases of cyber hacking can bring a lot of losses if you become a victim. Therefore, before a cyber hack happens to you, you should do some tips to avoid this crime.
Here are some tips to avoid cyber hacks:
- Use secure hosting
The most important tip is to use safe hosting, a safe website comes from using safe hosting too. Make sure your site uses hosting with a special layer of security.
After using secure hosting, the next tip is to regularly update, not only updates from the website side but also on your device’s operating system. Ensuring devices and systems are properly updated is one way to avoid cyber hacks.
When accessing a site, you must have seen a padlock icon in the upper left corner next to the URL address. The icon indicates that the site has used SSL.
SSL is a security certificate on a site that can help increase security in the data transfer process. Therefore it is important that you install SSL on the website.
Most account or system hacks are initiated due to weak and easy-to-guess passwords, so it is very easy for hackers to break through them. Therefore, from now on, use a unique password using a combination of numbers, letters, and special characters.
Who doesn’t know that with this authentication feature, 2FA is a security method with an additional layer on the website. So, to be able to log in, you don’t only need a password, but you have to verify it with a certain unique code.
For example, with a unique code from Google Authenticator, OTP code, or something else. This feature has been widely used in various large companies.
- Be careful when opening emails
Email is one of the media for online criminals to carry out their actions. Usually, these perpetrators will send emails to victims by pretending to be authorities.
There are many types of email content that are often used by online criminals, such as providing links that direct victims to click on them. If you are not vigilant enough, then you could be trapped in the evil plans they have prepared through this link.
Examples of Cyber Hack Cases in Indonesia
Indonesia is one of the targets of cyber hacks with claims of more than 500 million violations. According to attack data published by Kaspersky, Indonesia is a frequent target for ransomware. In Securelist’s daily data, Indonesia ranks 44th.
This means that the cyber security infrastructure in Indonesia is still inadequate and not evenly distributed. In the following, we summarize a list of cyber hack activities that have occurred in Indonesia, even causing a stir in the wider community.
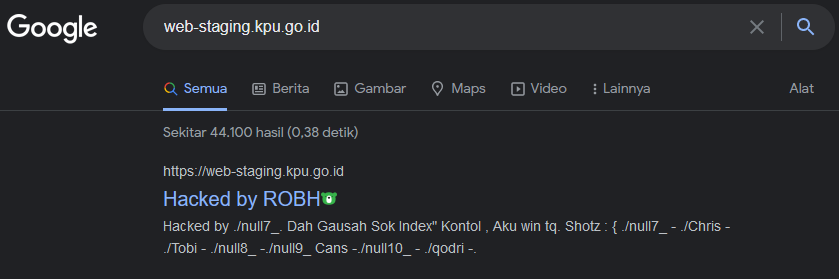
1. KPU Website (2004)
The KPU website is predicted to be a powerful website with a high level of security, because it has a large security budget, amounting to hundreds of billions.
But in fact, the KPU website was hacked by a hacker in a fairly simple way.
Hackers turned party names and logos into fruit. Until this article was published, there were still many cases of hacking, both regional KPU websites and web staging as follows.
2. Telkomsel Website (2017)
In April 2017, Telkomsel became the next victim of a cyber hack. The appearance of the website has changed, displaying harsh words as an expression of frustration at the high price of internet quota given by this internet provider.
3. Indonesia vs Australia Cyber Activists (2013)
This case, which has been going on for a long time, is already a public secret, where the main target was the President of the Republic of Indonesia at that time, namely Mr. Susilo Bambang Yudhoyono and his wife and ministers.
They have been spied on, or victims of Australian espionage since 2009 and the news was only published after former National Security Agency (NSA) employee Edward Snowden leaked it to the public.
This espionage incident received a response from various layers of society who criticized the Australian government. The relations between the two countries are increasingly heating up. In the aftermath, cyber activists in Indonesia carried out DoS attacks and defacements on business, hospital and government websites and Australian institutions, such as the police website.
4. Health BPJS (2021)
At the end of May 2021, a website belonging to the Social Security Administering Body (BPJS) for Health was allegedly the victim of a hack. In the aftermath, data belonging to 279 million Indonesians were allegedly leaked and sold on illegal data trading forums.
This data contains NIK, cellphone numbers, emails, addresses, to salary information, and is sold for 0.15 bitcoin (around IDR 84.4 million, exchange rate May 20, 2021).
5. BIN and 10 Indonesian Ministry Networks (2021)
In September 2021, internal network systems belonging to ten Indonesian ministries and state agencies, including those of the State Intelligence Agency (BIN), were reported to have been hacked.
This is known from the latest report by a group of internet security researchers belonging to international media, TheRecord, Insikt Group. Unfortunately, apart from BIN, the Insikt Group did not specify the names of the 9 networks of Indonesian ministries and state institutions that were the targets of the hack.
The Insikt Group only revealed that the hacking incident was related to Mustang Panda, a group of hackers from China who usually carry out espionage activities in cyberspace.
The target of its own operations is in the Southeast Asia region. However, BIN denied the hacking reports, saying that BIN’s servers were in a safe, controlled condition.
6. BSSN (2021)
Apart from the site owned by the Republic of Indonesia’s BPJS Kesehatan, the site owned by the National Cyber and Crypto Agency (BSSN) was also the victim of a hack by hackers using the deface technique in October 2021.
As for the BSSN property that was successfully broken into by the hackers, it was the National Malware Center (Pusmanas). According to the BSSN, the site contains data regarding malware reports or information (repositories).
7. POLRI Database (2021)
The final cyber-hack victim on this list is the POLRI website, which resulted in police data being leaked. The perpetrators of hacking this database were allegedly the same hackers on the BSSN website. The leaked data is sensitive information in the form of complete police data, starting from the name, address, rank to the violations that have been committed by these members.





